# Modular Arithmetic
Modular arithmetic is the foundation on which RSA is based.
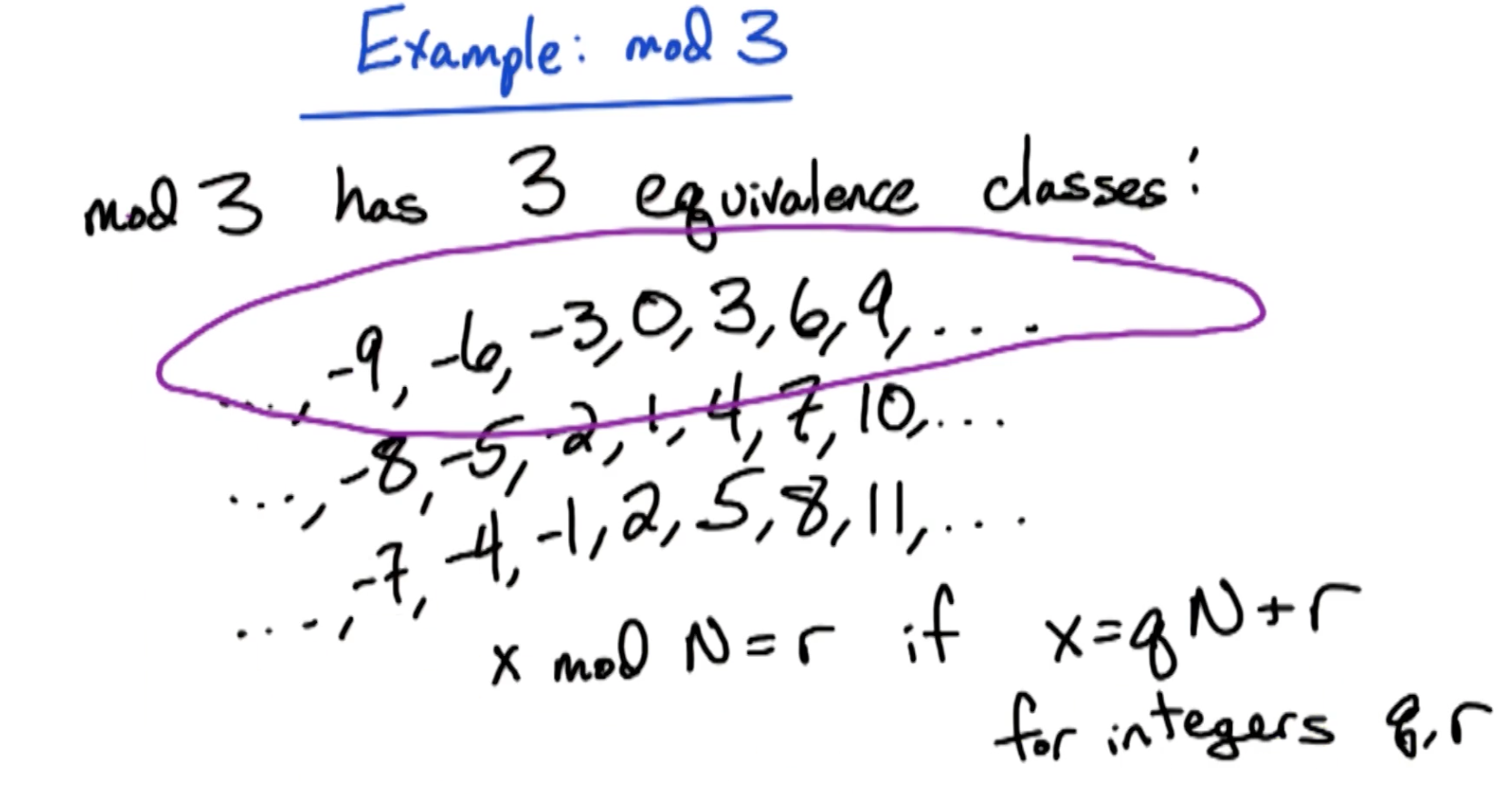
For integer
# Basic Fact
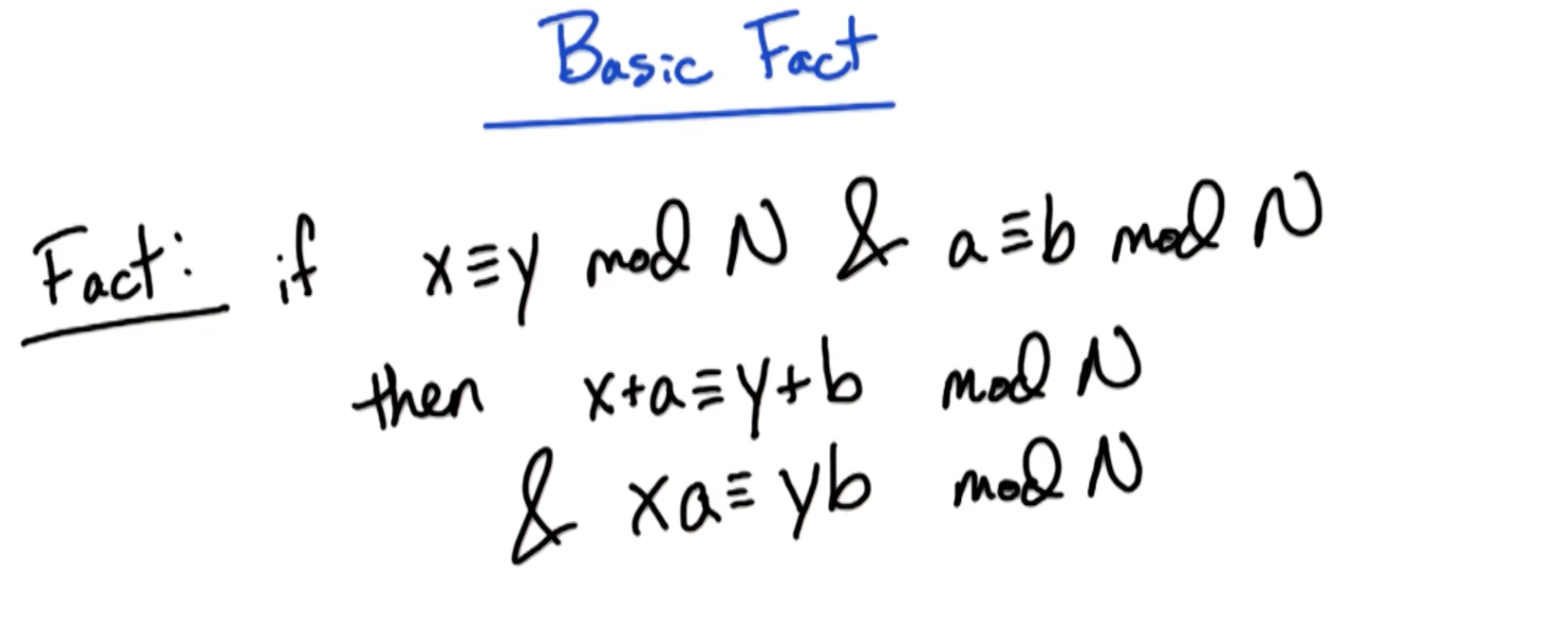
The above fact comes in handy to simplify and solve cases like the following:
321 x 17 mod 320

# Modular Exponentiation
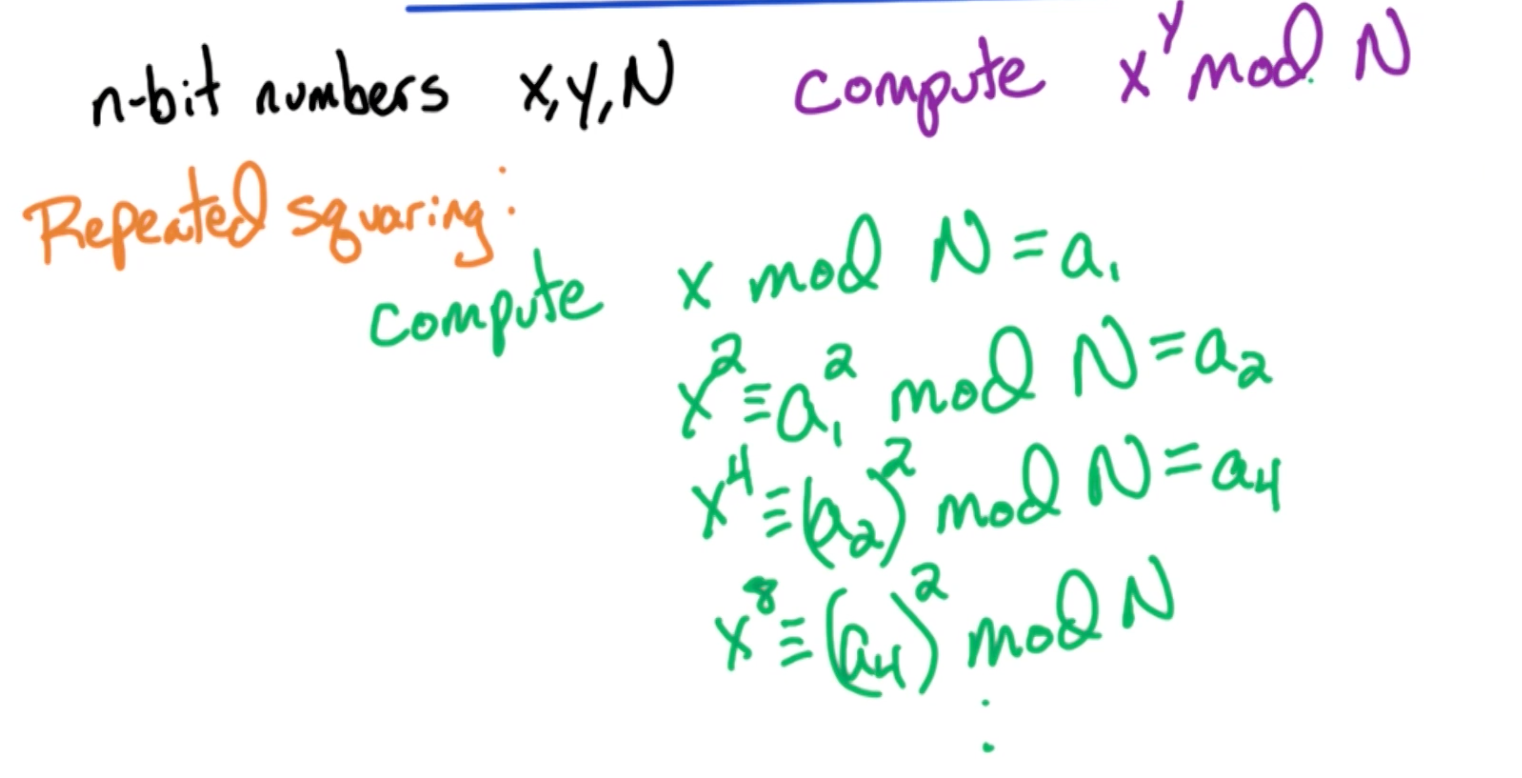
Example:

# Mod Ex. Algorithm

# Multiplicative Inverses
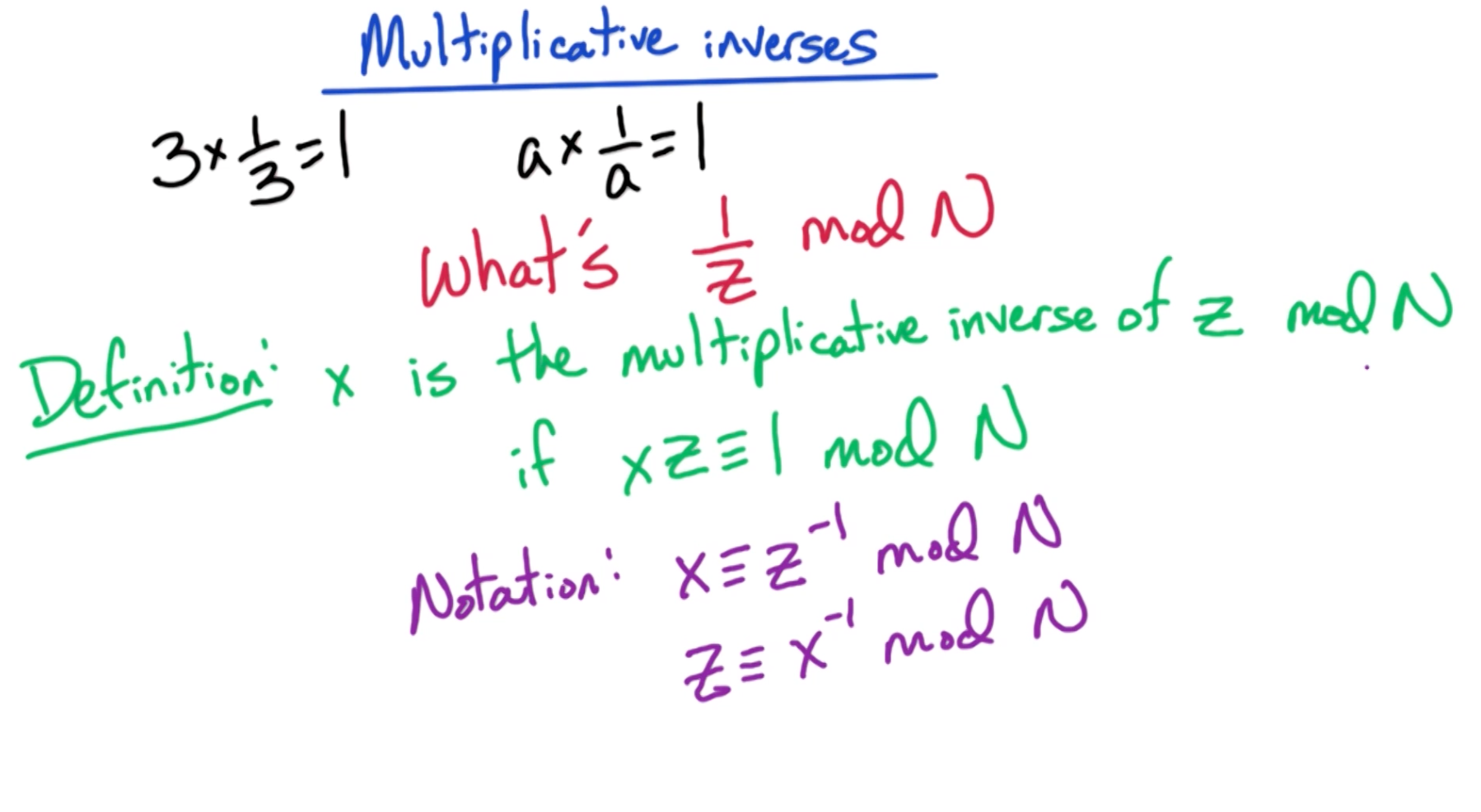
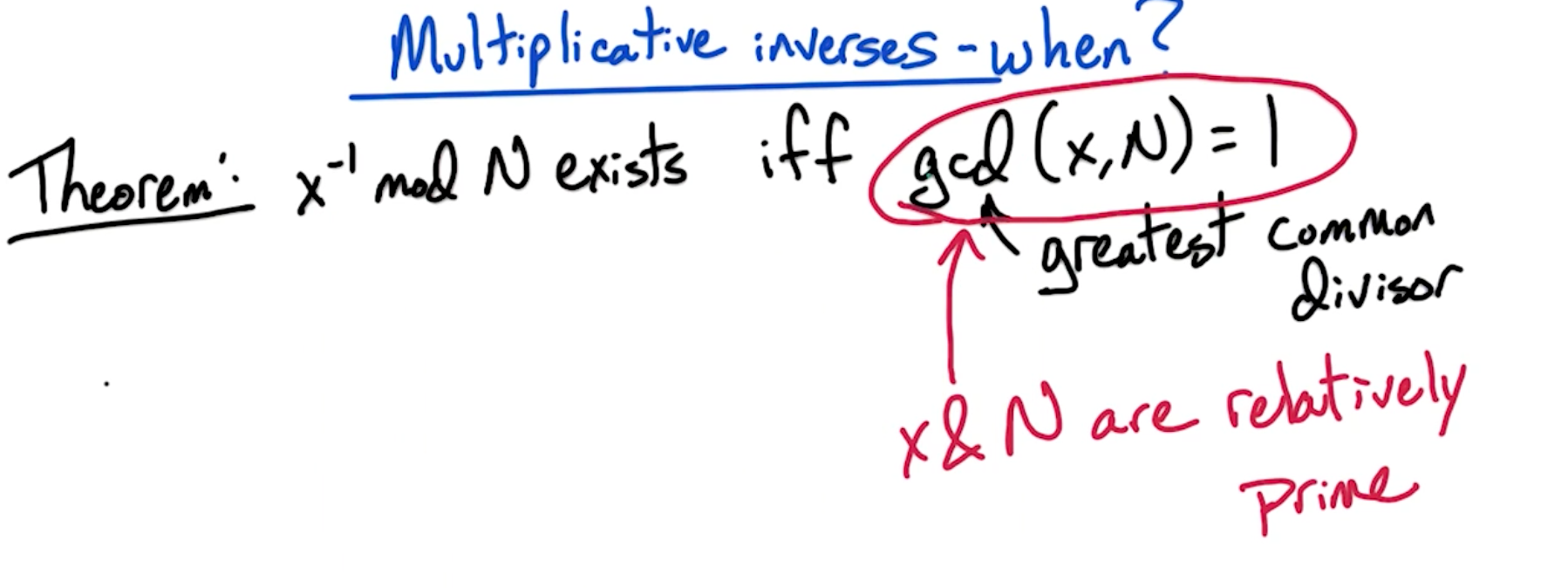
Multiplicative inverse of x exists iff the greatest common divisor of x and N is 1. This is also referred to as x and N being "relatively prime".
# Euclid's GCD Algorithm

The running time of this algorithm is
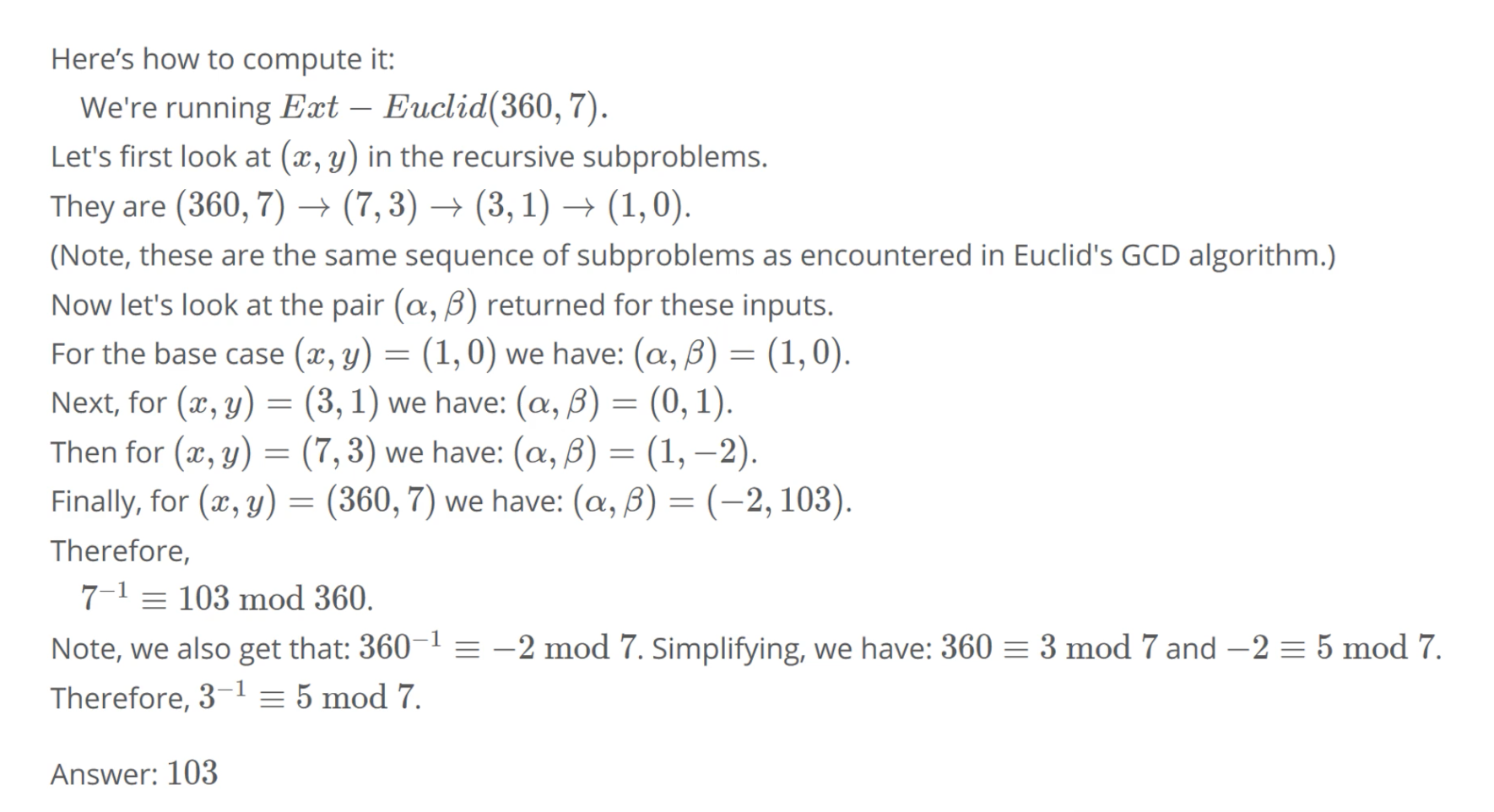
# Extended Euclid's Algo
For computing multiplicative inverses

The running time of this algorithm is
Using extended Euclid's algo, compute
# RSA
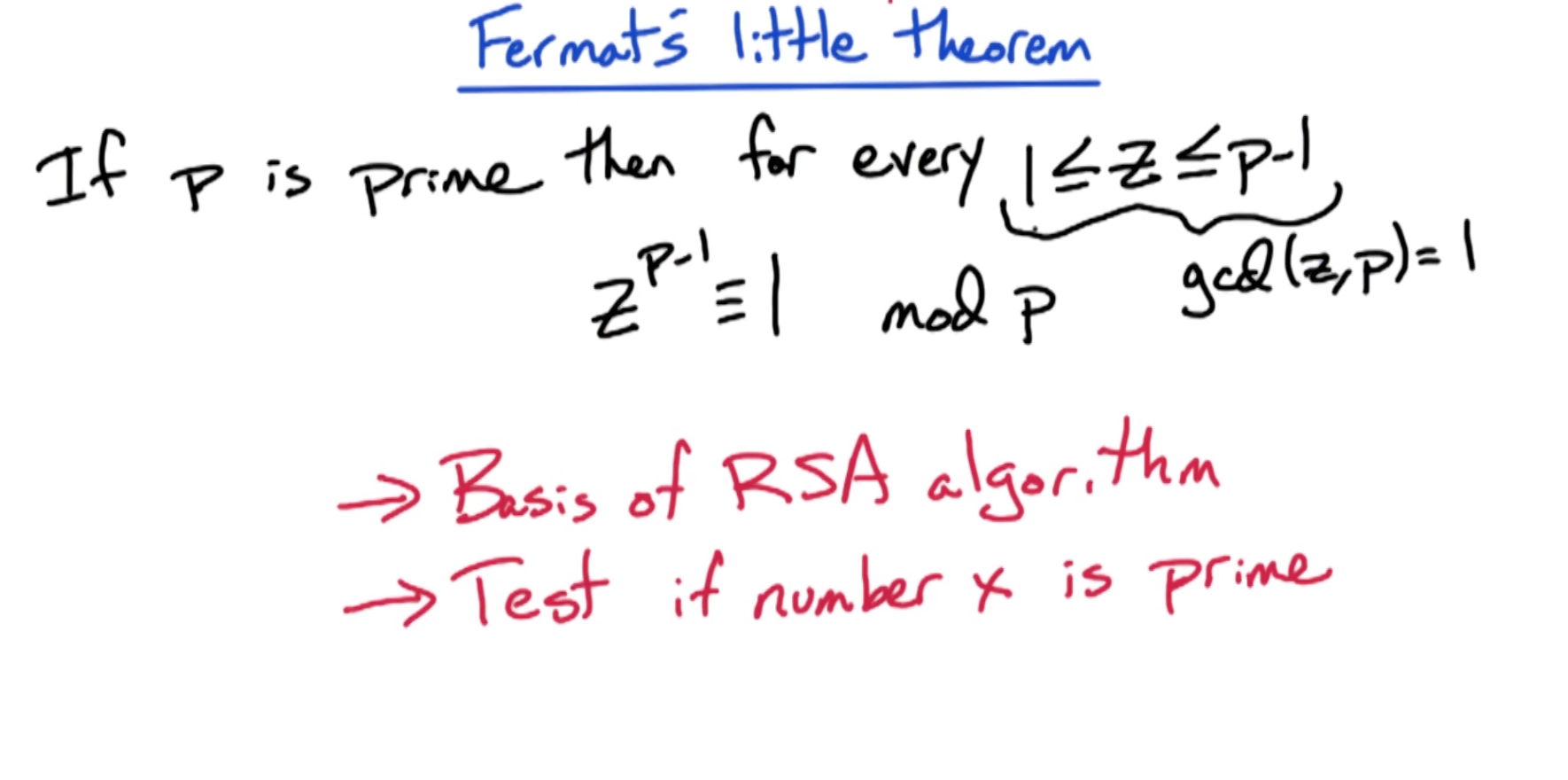
# Fermat's Little Theorem
# Euler's Theorem
It is a generalization of Fermat's little theorem.

For a prime number P,
# Euler's Theorem for N=pq
Likewise, for primes p and q, let N = pq.
In this case,
Therefore, for any z, where
And this is the fundamental idea that powers the RSA
# RSA Protocol: Receiver I
- Bob picks 2 n-bit random primes
pandq- This can be done by randomly generating a n-bit number and primality testing it
- Bob chooses
erelatively prime to (p-1)(q-1)- This means
using Euclid's Algorithm - Incrementally try with e=3,5,7,11...
- Let N = pq
- This means
- Bob publishes his public key (N, e)
- Bob computes his private key:
- We know
dexists because e is relatively prime to (p-1)(q-1) - We can compute
d, using extended euclid's algorithm
- We know
# RSA Protocol: Sender I
Alice wants to send message m to Bob
- Looks up Bob's public key (N, e)
- She computes
using fast modular exponentiation - She sends
y
# RSA Protocol: Receiver II
- Bob receives
y - Decrypts
yby computingto retrieve the original message, m
# RSA Pitfalls
When the encrypted message is computed,
If
pdividesmandpdividesn, thenpwill also dividey. In such a situation, a hacker can simply compute,and get psinceyis the encrypted message itself that is available, andNis part of public key. And then they can findqsincehence gathering all the info necessary to compute private key dand decrypt the messagem.mnot too largemtoo smallSending same
m,etimes - if the hacker can see all those encrypted messages, they can derive it.
# Practice Q
Given p = 13, and q = 31, what is the smallest encryption key and public Key (N, e)
The smallest encryption key e = 7.
Why?
Therefore, the next smallest prime is 7.
Public key
# Primality
Random primes are generated by randomly generating 0/1s for each bit of a n-bit number and checking if the overall number is a prime. Since primes are densely packed, we can expect to come across a prime number eventually after a few tries. However, the challenge is checking if the number is prime or not. And below is the discussion for it.
# Fermat's Test

# Better Primality

← Math Graph Theory →
